|
|
Flux Flow Racing - Florestapp - Claw Crane Confectionery - Head Doctor Games -
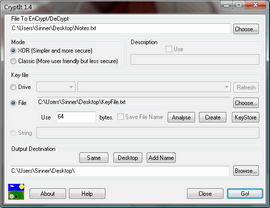 | Most file encryptors use methods that rely on the theory of computational security, that is the difficulty of key factorisation prevents decryption ofthe file. But this method may not work forever. It used to be considered that a 56 bit key was unbreakable to brute force attacks, but the government ...
|
 | Most file encryptors use methods that rely on the theory of computational security, that is the difficulty of key factorisation prevents decryption ofthe file. But this method may not work forever. It used to be considered that a 56 bit key was unbreakable to brute force attacks, but the government ...
|
XorIt (in Security)
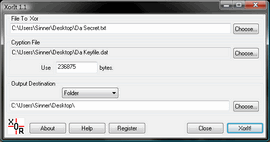 | Most file encryptors use methods that rely on the theory of computational security, that is difficulty of key factorisation prevents decryption of the file. But this method may not work forever. It used to be considered that a 56 bit key was unbreakable to brute force attacks, but the government of ...
|
XorIt (in Security)
 | Most file encryptors use methods that rely on the theory of computational security, that is difficulty of key factorisation prevents decryption of the file. But this method may not work forever. It used to be considered that a 56 bit key was unbreakable to brute force attacks, but the government of ...
|
|
|