|
|
Order by Related
- New Release
- Rate
Results in Title For sha 1 algorithm
 | Do you want to create your own program? Algorithm2 is a free tool for game and software development at home! With its help anybody can create a program without a knowledge of any programming language. .. |
|
 | We are proud to present you our unique image comparison algorithm implemented as standalone dll file. It has only one exported function with two bitmap pointers in and similarity percentage out. Can work with many programming languages including Delphi, Visual C++, C#, VB and VB.NET. We can also provide you with the modified DLL. It can precalculate image hash (768 bytes) and you can use these hashes for comparison then.
You can check our comparison algorithm with help of our Image Comparer tool. Use Google to quickly locate it. Command line version is also available. Custom versions are available too. ..
|
|
 | Object recognition technology for robotics and computer vision. Supports webcams, surveillance cameras, still image and video files. Tolerant to object scale, rotation, pose etc. Real-time video stream processing. The algorithm implements advanced visual-based object learning and recognition. Suitable for real-time applications like security systems, parts recognition in production lines, road signs recognition, image search engines etc. .. |
|
 | Demo application enrolls and identifies fingerprints from supported fingerprint scanners or image file, and can calculate ROC with custom fingerprint databases. Fingerprint recognition technology and software for PC and Mac. ..
|
|
 | The SDK is based on the VeriLook PC-based face identification technology. It can be used with most cameras, webcams and databases on Linux or Windows. Simultaneous multiple faces' detection, processing and identification up to 80,000 faces/second .. |
|
 | micro Dialer. Size 30Kb. Freeware. ..
|
|
Results in Keywords For sha 1 algorithm
 | This is an excellent file encryption tool in that it is very easy and quick to use. 'File Encryptor' is freeware... |
|
 | 30 day embedded SDK trial, allows developers to explore the SDK's possibilities and to try it in real environments and real applications.
Includes algorithm library, C/C++ programming samples, scanner drivers for Linux. Integration into ARM-based devices with ARM Linux or MS Windows Mobile.
Constant internet connection required during evaluation.
Commercial EDK types available:
the kit with ready-to-use hardware device for fast development,
the kit with algorithm library for ARM developers,
the kit with algorithm full source code for large-scale development using ARM-based or other embedded hardware.
For more information please review our web site or contact us...
|
|
 | Credit Card Checker Tool instantly check credit card number for validity. It verifies MasterCard, Visa, Carte Blanche, Diners Club, EnRoute, American Express (AMEX), Discover, JCB and other credit card numbers. Credit Card Check Tool utilizes LUHN10 algorithm (except EnRoute) and first card digits verification algorithm.
* Verifies MasterCard, Visa, American Express, Discover, Diners Club and many other card type numbers
* Uses LUHN10 checksum algorithm
* Performs first card digits identification
* Automatically determines type of the card.. |
|
 | Object recognition technology for robotics and computer vision. Supports webcams, surveillance cameras, still image and video files. Tolerant to object scale, rotation, pose etc. Real-time video stream processing. The algorithm implements advanced visual-based object learning and recognition. Suitable for real-time applications like security systems, parts recognition in production lines, road signs recognition, image search engines etc...
|
|
 | If you need a professional ciphered ZIP files creator, CypherZIP is your only choice. CypherZIP joins the reliability of the ZIP compression algorithm with Rijndael (the current AES) and DS2 algorithms. It is the unique to include the exclusive Paranoia Keyboard.. |
|
 | We are proud to present you our unique image comparison algorithm implemented as standalone dll file. It has only one exported function with two bitmap pointers in and similarity percentage out. Can work with many programming languages including Delphi, Visual C++, C#, VB and VB.NET. We can also provide you with the modified DLL. It can precalculate image hash (768 bytes) and you can use these hashes for comparison then.
You can check our comparison algorithm with help of our Image Comparer tool. Use Google to quickly locate it. Command line version is also available. Custom versions are available too...
|
|
 | Resize Pilot helps you resize photos quickly and easily. This photo resizing program has a unique algorithm for image enlarging. Sharpness of the image may slightly improve as a secondary effect of applying the algorithm... |
|
 | Service Process: You can run scheduled auto-recurring encryption and decryption sessions as a service process.
Encryption Scheduler: PrimaSoft Encryption utility comes with flexible scheduler. You can schedule auto recurring encryption sessions for any future date and time.
Encryption algorithms: AES (US Advanced Encryption Standard) secret-key encryption algorithm known as Rijndael. Certified by National Institute of Standards and Technologies (NIST). AES is the new official US government standard for encryption of data. Twofish encryption algorithm, a runner-up candidate for AES. RSA encryption is a public-key encryption algorithm.
Encryption compression and decompression: You can use the most popular ZIP archive file format within the Strong File Encryption / Decryption utility. You can define automatic compression and decompression of the encrypted or decrypted files.
Encryption Log: Our software maintains a detailed Activity Log so you can easily find out which encryption sessions were successful, which failed and why. Our program can send email notification with information about successful or failed file encryptions and decryptions... |
|
 | Reliable and convenient encryption software for files, using AES algorithm.
Features
1.Easy to use interface like MAC's GUI.
2.Can encrypt files of any type and any size.
3.Can encrypt files with strong AES algorithm.
4.Can encrypt more than one file at a time,can decrypt more than one file a time.
5.Adopt the international standard cryptographic algorithm--AES.
6.Support the 128,192,256-digit code in AES mode... |
|
 | This is our implementation of the famous MD5 algorithm, and presents an easy and highly secure way of verifying the integrity of files. Single-line text, multi-line text and file contents are all supported inputs. The resulting MD5 hash is displayed in a textbox for easy clipboard copying.
Software is often accompanied by an MD5 'hash' (or 'checksum'). This serves as a unique identifier for the contents of the file - if the file contents change then so does the MD5 hash, making it easy to verify the integrity of files.
A brief description of MD5:
The algorithm takes as input a message of arbitrary length and produces as output a 128 bit (16 byte) "fingerprint" of the input (also known as a "message digest", "checksum" or "hash"). It is conjectured that it is computationally infeasible to produce two messages having the same message digest, or to produce any message having a given prespecified target message digest. The MD5 algorithm was designed by Ron Rivest... |
|
Results in Description For sha 1 algorithm
 | File verification utility, uses SHA-2 algorithm... |
|
 | SHA-1 Password is a tool for security professionals, which allows recovering a password if you know its SHA-1 hash. The fast recovery engine can recover up to 32,000 passwords simultaneously...
|
|
 | This ActiveX OCX can compute very fast the checksum of strings or files using Adler32 , CRC32 , MD5 , SHA-1 and SHA-256 , the code is optimized for new AMD and Intel processors running very fast in the win32 environment.. |
|
 | Fast file checksum generation & verification tool. Supports MD2,MD4,MD5, SHA-1,SHA-2, RIPEMD-160,PANAMA,TIGER, CRC-32,ADLER32 algorithms and the hash used in eMule/eDonkey(ed2k). Compatible with md5sum,Easy MD5 Creator,SFV Checker/Verifier,Win CRC32...
|
|
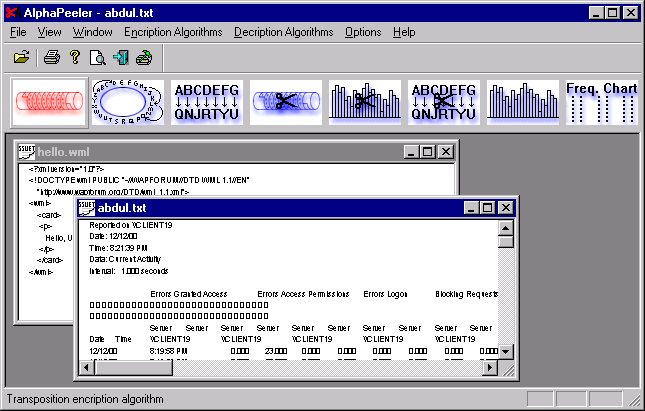 | AlphaPeeler Professional 1.0b (powered by crypto++) includes DES, Gzip/Gunzip, MD5, SHA-1, SHA-256, RIPEMD-16, RSA key generation, RSA crypto, RSA signature & validation, and generation of secret share files. Copyright .. |
|
 | Hyper Hasher is a small utility that allows you to calculate hash/checksum values for any file on your system, or text string. It combines the cryptography libraries built into the Microsoft .NET framework with the expansive Crypto++ cryptography library and other hashing libraries from around the internet.Features:-Hash Functions: MD2, MD4, MD5, SHA-1, SHA-256, SHA-384, SHA-512, HAVAL, Tiger, Panama, RIPEMD-160, FCS-16, FCS-32, GHash-32-3, GHash-32-5, GOST, Size32-Hash, emule/edonkey-Checksums: CRC16, CRC16-CCITT, CRC32, Adler32-Windows Shell Integration (optional)-Configuration Saving -Automatically compare two files.-Dump results to file.-Pentium 4 optimization.-Processor priority control. ..
|
|
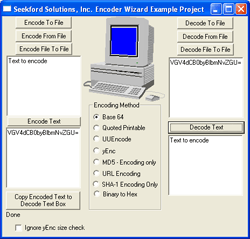 | Encoder Wizard is a collection of two ActiveX (ocx) controls, Encoder Wizard and Decoder Wizard. These two controls allow you to fully support the Base64, Quoted- Printable, UUEncode, yEnc, MD5,HMAC MD5, URL, SHA-1, and Binary 2 Hex encoding methods. You can Encode and Decode data quickly and intelligently. Base 64 is the Encoding Method usually used for Binary files in MIME messages. It is also used to encode data for special characters accross telnet connection to certain servers. Quoted-Printable is used to encode text for transmission accross certain mail servers. It is also commonly used in MIME messages. UUEncode is the data encoding mechanism used by Unix systems for encapsulating binary data so that it can transported safely accross network connections. yEnc is a recently created encoding method that is now used a lot in newsgroups since it is significantly more efficient for data storage than the UUEncode format. yEnc takes advantage of being able to use 8 bit encoding as opposed to the more restricted form of 7bit encoding used by UUEncode. MD5 is a message digest hash algorithm that is used for validation and verification of message integrity. It creates a highly unique 16 byte ( 128 bit ) digest from a set of data that is almost impossible to recreate without the same exact input data. HMAC MD5 is also supported. This allows for a "keyed" hash algorithm. The hash will only generate the same value when the data and key are the same. Great for integrity checks and secure hash generation. SHA-1 is another highly secure message digest algorithm used by the United States Government. It is now a publicly open algorithm which uses a 160 bit or 20 byte digest. The hash from any set of data less than 2^64 bytes in length provides a unique hash that is only creatable by the unique byte order... |
|
 | Encryptafile is an application that allows you to encrypt and decrypt data using the latest industry standard strong encryption algorithms. The application supports both traditional secret-key encryption as well as public-key encryption. For traditional strong encryption, Encryptafile supports the newly adopted AES (US Advanced Encryption Standard) secret-key encryption algorithm known as Rijndael which uses 128, 192 or 256-bit keys. It also supports the Twofish encryption algorithm, a runner-up candidate for AES. For public-key encryption (digital signing and verifying), the application offers the well-known RSA algorithm. Encryptafile also uses the modern SHA-2 and Haval hashing algorithms so that password/phrases can be converted to exactly the amount of bits required for an encryption key and with better mathematical properties than older hashing algorithms such as MD5. Like all XenoSystems products, this application is designed to be flexible yet extremely easy to use. In fact, it should take less time to figure out how to encrypt or decrypt files than the time it takes to read this page. The fully self-contained Task Constructor is all you need to perform encryption, decryption, signing, or verifying. That translates to minimal hassle at operation time. Encryptafile also supports all the available functionalities designed to make your job easier, such as categorized properties, built-in default properties, context-sensitive help, optional parameters, and built-in help documentation. We invite you to start integrating Encryptafile into your company, home business, or personal processes right away. All you really have to do is select a file and off you go!.. |
|
 | Dekart Private Disk Multifactor is an easy-to-use, secure and reliable disk encryption software. Provides 100% protection of private information without making you think about security. Dekart Private Disk Multifactor lets you easily and effectively eliminate the password risk and secure sensitive information. The software allows you to secure your disk(s) (including removable media) with a powerful and proven encryption algorithm (AES 256-bit), ensuring that only authorized users may access it. The algorithm has been certified by the National Institute of Standards and Technology as corresponding to Advanced Encryption Standard (AES) and Secure Hash Standard (SHA-1). Users can store their encryption keys on such widely spread removable storage devices as USB flash disks, pen drives and other removable storage media. Dekart Private Disk Multifactor allows enjoying the benefits of USB-Token or smart card authentication as well as the combination of smart card and biometric authentication (e.g. fingerpint scanner). The desired combination can be selected according to users requirements and available equipment. Multifactor authentication allows you to enjoy the benefits of strong authentication while not to be burdened by memorizing strong password... |
|
 | AlphaPeeler is a powerful tool for learning Cryptography and is used as educational tool at the faculty of Computer Engineering, SSUET. Students can easily learn frequency analysis and ciphers like Monoalphabetic substitution, Caesar and Transposition. AlphaPeeler Professional 1.0b (powered by crypto++ 4.1) also includes DES, Gzip/Gunzip, MD5, SHA-1, SHA-256, RIPEMD-16, RSA key generation, RSA crypto, RSA signature && validation, and generation of seceret share files. AlphaPeeler 1.0 was developed at Department of Computer Engineering, Sir Syed University of Engineering && Technology - Karachi (Pakistan). You can contact AlphaPeeler development group (alphapeeler@bigfoot.com) , for you software development, security and ecommerce requirements. Copyright ?1998-2001 .. |
|
Results in Tags For sha 1 algorithm
 | SHA-1 Password is a tool for security professionals, which allows recovering a password if you know its SHA-1 hash. The fast recovery engine can recover up to 32,000 passwords simultaneously... |
|
 | Easy and advanced encryption, decryption and hash ActiveX component for ASP or ASP.Net
Support encryption and decryption of file, string, memory buffer
Support calculation of hash on string, file or memory buffer
Support digital signature..
|
|
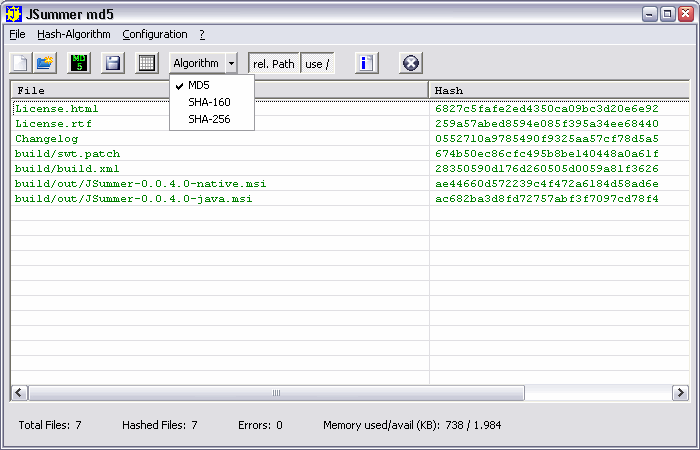 | JSummer is a tool to compute and check MD5, MD4, MD2, SHA-160, SHA-256, SHA-384, SHA-512, RIPEMD128, RIPEMD160, WHIRLPOOL, TIGER, HAVAL message digest. Console-Version and GUI. Implemented in Java... |
|
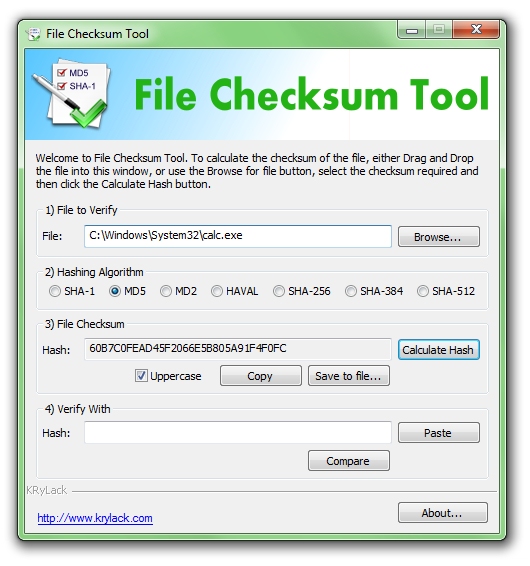 | File Checksum Tool is a free utility that calculates MD5, SHA-1, HAVAL, MD2, SHA-256, SHA-384, SHA-512 hash from a file. The software allows you to verify the Hash or create new checksum for your important data...
|
|
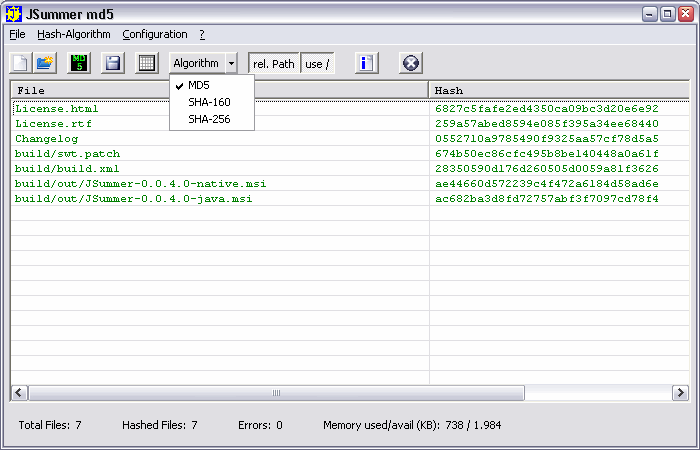 | JSummer is a tool to compute and check MD5, MD4, MD2, SHA-160, SHA-256, SHA-384, SHA-512, RIPEMD128, RIPEMD160, WHIRLPOOL, TIGER, HAVAL message digest. Console-Version and GUI. Implemented in Java... |
|
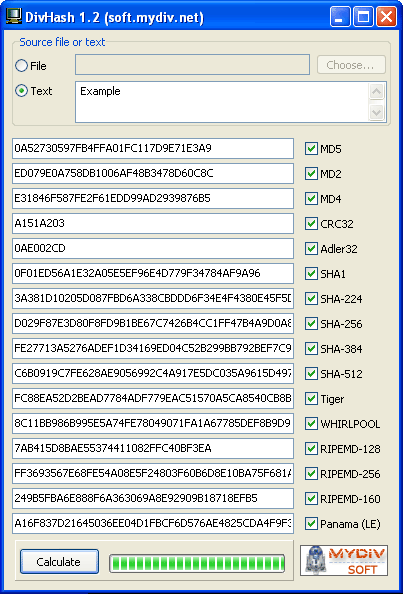 | Hashing and checksum operations for text or files. Algorithms for calculation: MD2, MD4, MD5, SHA1, SHA-224, SHA-256, SHA-384, SHA-512, RIPEMD-128, RIPEMD-160, RIPEMD-256, WHIRLPOOL, Tiger, Adler32, CRC32 and Panama..
|
|
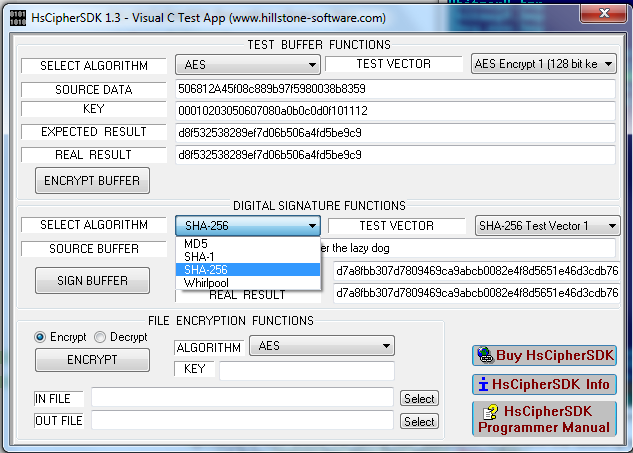 | HsCipherSDK is an Encryption Library providing an API of symmetric cryptographic algorithms and digital signing functions. The library includes block and stream cipher modules: AES, 3DES, ARC4, CAST-128, Blowfish,Twofish, MD5, SHA-1,SHA256,Whirlpool.. |
|
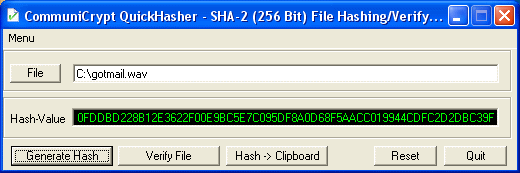 | With CommuniCrypt QuickHasher you can create a Hash value of a file or verify the authenticity of a file with an existing hash value. QuickHasher uses the modern SHA-2 Hash with 256 bit. The outdated MD5 is not supported. Requires VB6 runtime!.. |
|
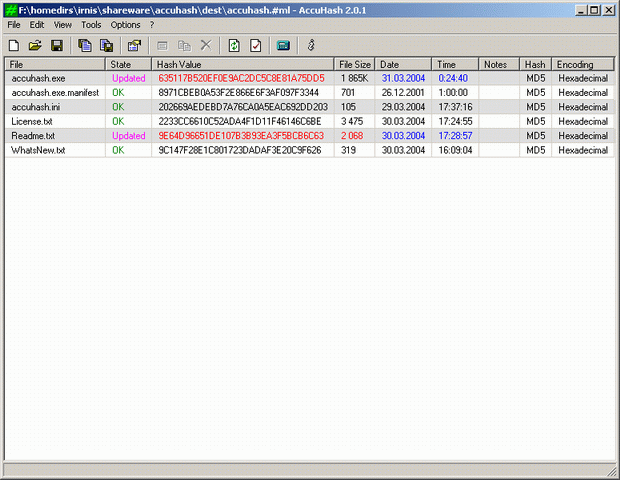 | Utility for protecting the integrity and verifying the accuracy of data files using checksum calculation algorithms, uses XML-based and Unicode-enabled checksum file format, and has the integrated checksum calculator. Supports the SFV and MD5SUM... |
|
 | MSCCrypto includes collection of the best encryption and hashing algorithms: RSA, AES, Blowfish, Twofish, MD5, SHA1 and 32-bit CRC checksum. Includes PGP/OpenPGP compatible component.. |
|
Related search : ncryption andalgorithm likesupport encryptionmd5 shahash algorithmultra cryptocrypto component,ultra crypto componentsha sha256 sha384sha256 sha384 sha512memory buffer supporthash algorithm likeaes128 aes192 aes256des 3des 3des23des 3des2 aes1283des2Order by Related
- New Release
- Rate
algorithm used -
algorithm 2 -
algorithm -
hash algorithm -
recursive algorithm -
|
|


























